ICE Sustainable Finance Insights: Access our latest insights and research. Learn more

Climate Data
Climate change poses a major risk to the stability of the global financial system. ICE Climate Data integrates climate data and analytics for corporates, municipals and mortgage-backed securities, which can help investors and companies to identify, measure and understand physical climate and transition risks.
Climate Physical Risk Data
Geospatial climate, economic and demographic data to help investors quantify climate risk exposure across municipal bond and MBS portfolios.

Climate Transition Analytics Data
Climate scenario analysis, emissions and targets data to help financial institutions develop decarbonization strategies.

Climate Physical Risk Data
Geospatial climate, economic and demographic data to help investors quantify climate risk exposure across municipal bond and MBS portfolios.

Climate Transition Analytics Data
Climate scenario analysis, emissions and targets data to help financial institutions develop decarbonization strategies.

Climate Physical Risk Data
With extreme weather events on the rise there is increasing concern over how the U.S. municipal bond and mortgage-backed security MBS, which may be particularly vulnerable to physical events, will manage these challenges. Climate and ESG data may be able to provide an added layer of transparency into the risks and opportunities in these markets.
- Extensive coverage of U.S. municipal and MBS market: CUSIP-level coverage of ~98% of the ~$4T in outstanding municipal debt and ~95% coverage of the U.S. MBS universe
- Scores: To allow for ease of comparison, scores are available. The ICE Climate Risk Score is a unified metric on a scale of 0-5 used to compare securities, assess portfolios and benchmark to indices. The Score is built from ICE Flood Score, ICE Wildfire Score and ICE Hurricane Score
- Weekly climate risk commentary on new issuances
- Climate action plans: An expansive database on state and local government climate resilience planning
Flexible delivery options include a file-based solution at the security level, allowing for integration into risk systems and other analytical tools, as well as a web user-interface:
- Customizable capabilities allow for user-defined searches and templates
- Downloadable visuals and the ability to generate custom reports
- Portfolio analytics with daily alerts for wildfire and hurricane events
ICE ESG Geo-Analyzer is a visualization and analytics solution that enables data-driven actionable insights for location-linked assets. Users can analyze climate and social features surrounding any specific location within the continental United States, regardless of the presence of any linked security.
The Geo-Analyzer provides climate risk and demographic metrics at property-level. It can be used to analyze client provided locations, such as pre-securitized commercial properties, whole loan portfolios, and real estate holdings, and their respective associated location-backed securities.
- Comprehensive U.S. coverage: Access climate risk and social impact data for any continental U.S. location
- Custom inputs: Climate risk, social, and demographic data aggregated for any user-provided location (latitude & longitude) within the continental U.S.
- Portfolio summary: Portfolio-level (or pool-level) ICE Climate Risk scores and ICE Social Impact scores
- On-demand: Retrieval of files and/or output from a self-service user interface
- Flexible delivery options including web-based user interface and API, allowing for time-sensitive applications
- NAICS workforce information
- ICE Climate Risk Score
- ICE Flood Score, ICE Wildfire Score and ICE Hurricane Score
- ICE Social Impact Score
- Community affluence scores
- Community demographic information
- Community health obstacle scores
- Over 100+ other fields
Leveraging ICE Sustainable Finance data and DeltaTerra Klima®, ICE DeltaTerra Climate Credit Analytics is the translation of physical climate risk estimates into financial risk assessments, helping to address the specific needs of investors in securitized bond markets.

Physical climate risk data with market data on insurance, realized damages, property prices, mortgage performance, bond prices, and economics, is inputted within DeltaTerra Klima® to produce ICE DeltaTerra Climate Credit Analytics, an estimate of climate-driven scenario value correction for properties, loans, and MBS securities.
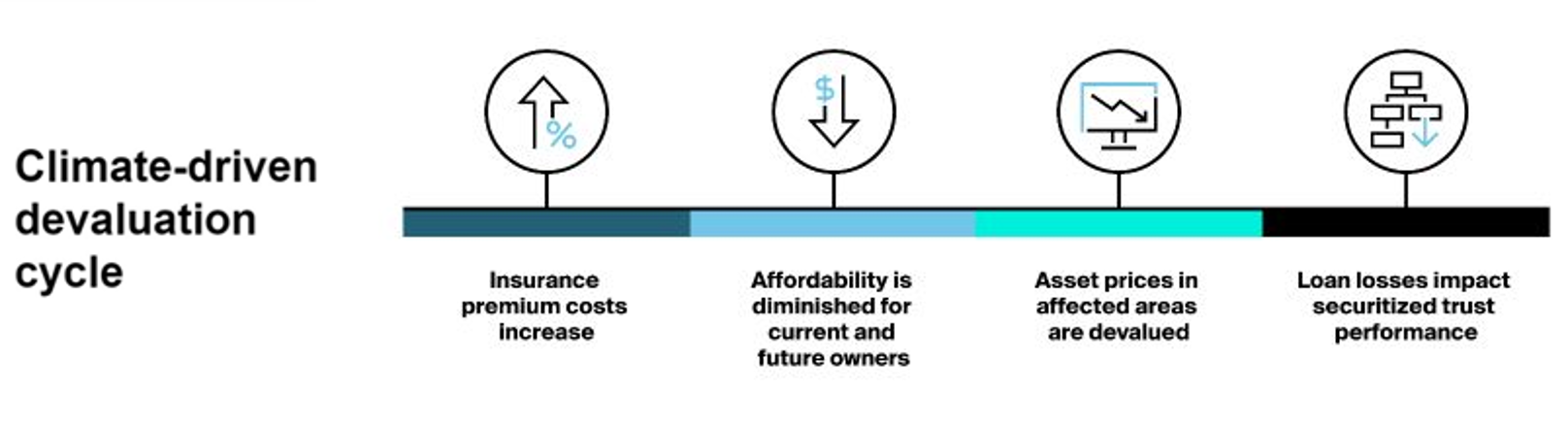
- Bond intrinsic value impact in Base and Bear scenarios of insurance cost increases and property value declines
- Asset price depreciation risk from flood & fire exposure
- Climate-adjusted DTI/DSCR & LTV
- Loan expected default frequency & loss given default
- Pool expected loss distribution
- Investment Analysis
- Portfolio Risk Management
- TCFD-aligned Reporting
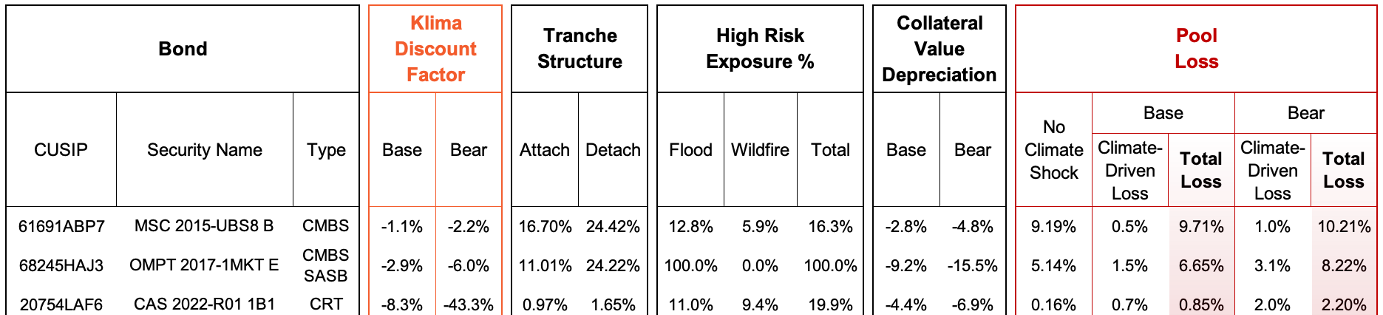
- Fannie Mae Connecticut Avenue Securities (CAS)
- Freddie Mac Structured Agency Credit Risk (STACR)
- Conduit/Fusion
- Single Asset Single Borrower (SASB)
Climate Transition Analytics Data
The global transition to a low carbon environment creates risks and opportunities for financial market participants. Adoption of net zero strategies and other responses to climate change, will see a huge reallocation of capital, reshaping businesses and policy.
Emissions and Targets Data can help companies and financial institutions understand the climate risk landscape, meet regulatory requirements and capitalize on climate-related opportunities.
- Scope 1: Gross emissions
- Scope 2: Market-based and location-based emissions
- Scope 3: Emissions, broken down by 15 disclosure categories
- Absolute and intensity values: tCO2e and tCO2e/$m revenue/market value/EVIC
- Companies classified into proprietary disclosure categories, providing insight on data quality
- Information on third-party assurance of emissions data
- Outlier detection
- Regional and country level analysis
- Emission Reduction Targets Data is cross-referenced with GHG Emissions Data to enhance coverage
- 5,500 global companies analysed for reported emissions data
- Modelled data for 30,000+ companies using statistical models based on a quality assured dataset of analysed companies
- Both listed and unlisted securities covered, including equities, corporate and government bonds, and loans
- Emissions data spanning from 2010
- Transparency on differentiating between disclosed and modelled data, and methodologies used
- Coverage can be expanded to help meet client requirements on a bespoke basis
- 2,500+ global companies covered
- Reported Targets extending to the year 2100
- Absolute and Intensity based targets
- Includes directly collected targets as well as SBTi datasets
The Climate Transition Analytics Tool, which is part of the ICE Sustainable Finance Platform, integrates climate data and science-aligned analytics at a company, sector and portfolio level. Designed by climate risk specialists, the tool helps asset owners, asset managers, investors and companies identify, measure and understand the potential climate risks and opportunities within portfolios and loan books.
- 5,500 global companies analysed for reported emissions data
- Modelled data for 30,000+ companies using statistical models based on a quality assured dataset of analysed companies
- Granular, company level emissions data
- Reported and Modelled GHG Protocol defined Scope 1, 2 & 3 emissions data
- All 15 categories of Scope 3
- 10-year Emissions Database
- Carbon footprinting
- Scope 3 materiality
- Temperature alignment
- Paris agreement
- Target setting
- Avoided emissions
Explore the four motivations driving usage
Related insights
Exploring the intersection of real estate carbon emissions and housing affordability
The skyrocketing cost of housing affects people across the United States, particularly lower to middle income residents[1]. Many households also struggle to pay their energy bills, adding to their cost burden. Could better energy efficiency provide housing cost relief while also cutting emissions? In this paper, we explore the contribution of real estate to global carbon emissions, and tools that may lead to a better understanding of the intersection between the two.
Climate risks - beyond the physical
The mention of ‘Climate Risk’ inevitably turns our thoughts to dramatic weather events such as floods, storms, hurricanes as well as drought and forest fires (“Physical Climate Risk”). These often-devastating Physical Climate Risk events grab the media’s attention and are widely reported. However, there is another kind of Climate Risk which is much less discussed and not as widely covered in the mainstream media, despite the potential for it to impact every part of daily life: Climate Transition Risk.
The U.S. municipal bond market does not price in physical climate risk
As concern about climate risk disclosure grows, an analysis of ~800,000 U.S. municipal bonds representing over $2.5T in outstanding debt shows no evidence it is being systematically priced in. Yet event-based climate risk is correlated with discounts in both property value appreciation and population growth over the past decade – the pillars of municipal market tax revenue and stability.
Climate & Capital Conference session replays
As part of Climate Week, we held the inaugural Climate and Capital Conference at the New York Stock Exchange, an ICE exchange. The event - hosted by ICE, Gitterman Asset Management and FINTECH.TV - brought together industry leaders to talk climate risks and opportunities. They discussed topics like aligning capital with climate commitments, ways to engage with corporate issuers on decarbonization strategies and solutions to measure and manage climate risk. Sessions and additional resources are now available on-demand.
Exploring the intersection of real estate carbon emissions and housing affordability
The skyrocketing cost of housing affects people across the United States, particularly lower to middle income residents[1]. Many households also struggle to pay their energy bills, adding to their cost burden. Could better energy efficiency provide housing cost relief while also cutting emissions? In this paper, we explore the contribution of real estate to global carbon emissions, and tools that may lead to a better understanding of the intersection between the two.
Climate risks - beyond the physical
The mention of ‘Climate Risk’ inevitably turns our thoughts to dramatic weather events such as floods, storms, hurricanes as well as drought and forest fires (“Physical Climate Risk”). These often-devastating Physical Climate Risk events grab the media’s attention and are widely reported. However, there is another kind of Climate Risk which is much less discussed and not as widely covered in the mainstream media, despite the potential for it to impact every part of daily life: Climate Transition Risk.
The U.S. municipal bond market does not price in physical climate risk
As concern about climate risk disclosure grows, an analysis of ~800,000 U.S. municipal bonds representing over $2.5T in outstanding debt shows no evidence it is being systematically priced in. Yet event-based climate risk is correlated with discounts in both property value appreciation and population growth over the past decade – the pillars of municipal market tax revenue and stability.
Climate & Capital Conference session replays
As part of Climate Week, we held the inaugural Climate and Capital Conference at the New York Stock Exchange, an ICE exchange. The event - hosted by ICE, Gitterman Asset Management and FINTECH.TV - brought together industry leaders to talk climate risks and opportunities. They discussed topics like aligning capital with climate commitments, ways to engage with corporate issuers on decarbonization strategies and solutions to measure and manage climate risk. Sessions and additional resources are now available on-demand.